TECH
TheJavaSea.me Leaks AIO-TLP287: Exposing the Data Breach and Its Consequences
 In an era where cybersecurity threats are becoming increasingly sophisticated, data breaches have become a major concern for individuals, businesses, and governments. The recent TheJavaSea.me leaks AIO-TLP287 has sparked widespread discussions in the cybersecurity community, raising alarms about data privacy, security vulnerabilities, and the risks of online information leaks.
In an era where cybersecurity threats are becoming increasingly sophisticated, data breaches have become a major concern for individuals, businesses, and governments. The recent TheJavaSea.me leaks AIO-TLP287 has sparked widespread discussions in the cybersecurity community, raising alarms about data privacy, security vulnerabilities, and the risks of online information leaks.
This article provides a comprehensive breakdown of TheJavaSea.me data breach, analyzing its origins, affected data, implications for users and organizations, and measures to safeguard against future attacks.
Understanding TheJavaSea.me and AIO-TLP287
What is TheJavaSea.me?
TheJavaSea.me is an online platform that has gained notoriety for allegedly hosting and sharing leaked content, including hacked databases, confidential corporate records, and compromised user credentials.
While details about its administrators remain unclear, the platform operates in a legal gray area, often used for the unauthorized distribution of sensitive data.
What Does AIO-TLP287 Mean?
The term AIO-TLP287 remains ambiguous, but cybersecurity experts suggest the following interpretations:
- AIO (All-In-One) – Indicates a compiled database leak containing multiple types of information rather than a single dataset.
- TLP287 – May refer to a Traffic Light Protocol (TLP) classification, a system used in cybersecurity to define information-sharing restrictions. However, the exact meaning of “287” remains unknown.
This suggests that TheJavaSea.me leaks AIO-TLP287 is a massive, multi-source data breach that aggregates various datasets into one major leak, making it particularly concerning.
What Information Was Exposed in the AIO-TLP287 Leak?

Although the full extent of the breach is still being analyzed, leaked data may include:
User Credentials – Email addresses, usernames, and passwords (possibly in plaintext).
Financial Data – Credit card numbers, banking details, and transaction logs.
Corporate Documents – Leaked company files, internal communications, and employee data.
Software & Proprietary Code – Cracked applications, leaked scripts, and development tools.
Personal Information – Sensitive user data that could lead to identity theft and fraud.
The presence of such a diverse range of data could have serious consequences for individuals, businesses, and even government agencies.
The Impact of TheJavaSea.me Leaks AIO-TLP287
For Individuals
Identity Theft – Stolen personal data could be misused for fraud, impersonation, and scams.
Financial Fraud – Exposed banking information could lead to unauthorized transactions and credit card fraud.
Account Takeovers – Hackers may use leaked passwords for credential stuffing attacks, compromising multiple online accounts.
Doxxing & Harassment – Leaked personal details can be weaponized for cyberbullying, harassment, or blackmail.
For Businesses & Organizations
Legal & Regulatory Penalties – Companies could face lawsuits, fines, and sanctions if they fail to protect user data.
Reputation Damage – Customers lose trust when businesses suffer security breaches.
Financial Losses – Organizations may incur massive costs from cyberattacks, regulatory fines, and security upgrades.
Operational Disruptions – Businesses may need to shut down affected systems to contain the breach.
For the Cybersecurity Industry
Increased Cybercrime Activity – More dark web trading of stolen credentials may emerge.
New Attack Vectors – Hackers could exploit leaked information for future breaches and social engineering attacks.
Rising Cybersecurity Costs – Companies will be forced to invest more in cybersecurity solutions to prevent similar incidents.
Community & Expert Reactions to the Leak
Public Concerns
Many affected users are expressing frustration and fear over the exposure of their personal and financial data. Social media platforms and cybersecurity forums are flooded with discussions on how to protect themselves from potential cyber threats.
Cybersecurity Experts Weigh In
Stronger Encryption Needed – Companies must ensure sensitive data is encrypted to prevent easy access in case of a breach.
User Vigilance is Key – Individuals must change compromised passwords and enable two-factor authentication (2FA).
Proactive Security Measures – Businesses should conduct frequent security audits and penetration testing.
Legal & Regulatory Implications
Governments and regulatory bodies are likely to investigate the breach and enforce data protection laws such as:
GDPR (General Data Protection Regulation) – Europe
CCPA (California Consumer Privacy Act) – United States
PIPEDA (Personal Information Protection and Electronic Documents Act) – Canada
Failure to comply with these regulations could result in heavy fines and legal actions for companies found responsible for mishandling user data.
How to Protect Yourself from Data Breaches
For Individuals
Check if You Were Affected – Use breach notification services like Have I Been Pwned to see if your data was compromised.
Update Passwords – Use strong, unique passwords for every online account. A password manager can help.
Enable Two-Factor Authentication (2FA) – Adds an extra layer of security to prevent unauthorized access.
Watch for Phishing Scams – Hackers may use leaked data to craft convincing phishing emails.
For Businesses
Implement Multi-Layered Security – Use firewalls, intrusion detection systems, and endpoint security solutions.
Encrypt Sensitive Data – Ensures that even if hackers access files, the data remains unreadable.
Conduct Regular Security Audits – Hire ethical hackers to test for vulnerabilities.
Develop an Incident Response Plan – A well-structured plan can minimize damage and speed up recovery efforts.
The Future of Cybersecurity After TheJavaSea.me Leaks AIO-TLP287
Advancements in Cybersecurity Technology
- AI-Driven Security – Artificial intelligence is being used to detect anomalies and prevent cyberattacks.
- Zero-Trust Architecture – Organizations are moving towards a zero-trust security model to reduce attack risks.
- Biometric Authentication – Fingerprints and facial recognition may replace passwords in the future.
Stronger Government Regulations
Governments worldwide are introducing stricter cybersecurity regulations, ensuring businesses take data protection more seriously.
Conclusion
The TheJavaSea.me leaks AIO-TLP287 serves as a stark reminder of the ongoing risks posed by cyber threats. Whether you are an individual, a business owner, or a cybersecurity expert, understanding the impact of such breaches and taking proactive security measures is crucial.
By prioritizing stronger cybersecurity protocols, user awareness, and continuous innovation in security technologies, we can better protect ourselves against future data leaks and cyberattacks.
FAQs About TheJavaSea.me Leaks AIO-TLP287
What is TheJavaSea.me Leaks AIO-TLP287?
TheJavaSea.me Leaks AIO-TLP287 refers to a massive data breach associated with the website TheJavaSea.me, which has allegedly leaked sensitive user credentials, financial data, corporate records, and proprietary software.
What kind of information was exposed in the AIO-TLP287 leak?
The leaked data may include:
User Credentials – Email addresses, usernames, and passwords.
Financial Information – Credit card details and banking records.
Corporate Data – Internal reports, confidential emails, and private documents.
Software & Proprietary Code – Cracked applications and scripts.
Who is affected by TheJavaSea.me Leaks AIO-TLP287?
The breach may impact:
Individuals whose personal and financial data have been exposed.
Businesses that store customer data and proprietary information.
Cybersecurity experts & regulators who must respond to the incident.
How can I check if my data was leaked?
You can use breach notification tools like:
Have I Been Pwned
DeHashed
LeakCheck
Enter your email address or username to see if it appears in any known breaches.
What should I do if my information was leaked?
Change your passwords immediately – Use strong, unique passwords for each account.
Enable Two-Factor Authentication (2FA) – Adds extra security to your accounts.
Monitor bank accounts & credit reports – Watch for suspicious activity.
Be cautious of phishing scams – Hackers may use leaked data for fraud.
What are the risks of this data breach?
Identity Theft – Cybercriminals can misuse stolen personal data.
Financial Fraud – Leaked banking details may lead to unauthorized transactions.
Credential Stuffing Attacks – Hackers try leaked passwords on multiple sites.
Doxxing & Harassment – Exposure of private details may lead to cyberstalking.
Can businesses prevent such breaches?
Yes! Organizations should:
Encrypt sensitive data to prevent unauthorized access.
Regularly update security protocols and perform penetration testing.
Train employees on cybersecurity best practices to avoid phishing attacks.
Monitor for unusual activity using AI-driven security tools.
Is TheJavaSea.me still operational?
It is unclear whether TheJavaSea.me is still active or has been taken down. However, leaked data from the breach may still be circulating on the dark web.
Will legal action be taken against TheJavaSea.me?
Government agencies and regulatory bodies may investigate the breach and impose fines, sanctions, or criminal charges on responsible parties.
What cybersecurity measures can individuals take to stay safe?
Use a password manager – Avoid reusing passwords.
Keep software & devices updated – Prevent vulnerabilities.
Enable multi-factor authentication (MFA) – Add an extra layer of protection.
Avoid clicking suspicious links – Phishing attacks are common after breaches.
What does this breach mean for the future of cybersecurity?
TheJavaSea.me Leaks AIO-TLP287 highlights:
The growing threat of cybercrime and data breaches.
The need for stricter cybersecurity regulations and enforcement.
The importance of proactive security measures for individuals and businesses.
Where can I find more information about TheJavaSea.me Leaks AIO-TLP287?
For updates and security alerts, follow:
Cybersecurity news websites
Dark web monitoring tools
Official security advisories from government agencies
TECH
Exploring #milestoneareacom/: What You Need to Know

 In today’s fast paced digital world, hashtags and online communities have become essential tools for discovering information, connecting with like minded people, and keeping up with trends. One such term gaining attention is #milestoneareacom/. Whether you’re a casual browser, a potential customer, or simply curious, understanding what this hashtag represents can help you navigate its significance online.
In today’s fast paced digital world, hashtags and online communities have become essential tools for discovering information, connecting with like minded people, and keeping up with trends. One such term gaining attention is #milestoneareacom/. Whether you’re a casual browser, a potential customer, or simply curious, understanding what this hashtag represents can help you navigate its significance online.
What is #milestoneareacom/?
At its core, #milestoneareacom/ is a digital marker used to highlight updates, announcements, and discussions related to the Milestone Area platform. While details about the exact nature of the platform vary, it is commonly associated with:
-
Real estate developments
-
Community projects
-
Innovative digital solutions
-
Updates and milestones within a specific business or project
The use of a hashtag like #milestoneareacom/ ensures that content is easily discoverable across social media platforms, making it a hub for engagement and conversation.
Why People Use #milestoneareacom/
There are several reasons why users search for or use #milestoneareacom/ online:
-
Stay Updated: Followers can track the latest developments in real time.
-
Community Engagement: Users can connect with others who are interested in the same project or topic.
-
Marketing & Promotion: Businesses and project owners use hashtags to boost visibility and attract potential clients or investors.
-
Information Sharing: It helps people share news, images, and content related to milestones or achievements.
This hashtag serves as a bridge between digital updates and real-world impact, creating a sense of connectedness among users.
Benefits of Following #milestoneareacom/
Following or searching for #milestoneareacom/ online can offer several benefits:
-
Quick Access to Updates: Stay ahead of news or releases.
-
Networking Opportunities: Connect with professionals, enthusiasts, or residents in a specific area.
-
Transparency: Businesses or projects using the hashtag often post updates, creating trust and reliability.
-
Event Announcements: Users can learn about upcoming events, launches, or milestones in advance.
How to Engage with #milestoneareacom/
Engaging with this hashtag is simple and can be done across social media platforms:
-
Search the Hashtag: Platforms like Instagram, Twitter, and LinkedIn allow users to search hashtags directly.
-
Follow Accounts Using the Hashtag: Engage with pages or profiles actively posting about #milestoneareacom/.
-
Comment and Share: Contribute to discussions or share posts with your network.
-
Monitor Trends: Keep an eye on the hashtag for patterns, updates, and announcements.
By interacting thoughtfully, users not only stay informed but can also expand their network and visibility within relevant communities.
Tips for Businesses Using #milestoneareacom/
If you manage a project or business connected to #milestoneareacom/, consider the following strategies:
-
Regular Updates: Consistently post updates, images, or news to maintain engagement.
-
User-Generated Content: Encourage followers to share their experiences using the hashtag.
-
Interactive Posts: Use polls, questions, or contests to boost interaction.
-
Cross-Promotion: Share the hashtag across multiple platforms for maximum reach.
A well-managed hashtag strategy can improve brand recognition, customer loyalty, and online visibility.
Conclusion
While #milestoneareacom/ may seem like just another hashtag, its purpose is far greater. It serves as a centralized digital space for updates, engagement, and community building. Whether you are a curious individual, a potential investor, or a business owner, understanding and utilizing #milestoneareacom/ can help you stay connected, informed, and engaged.
In the era of social media and digital marketing, hashtags like #milestoneareacom/ are powerful tools that turn ordinary updates into widely discoverable, meaningful conversations.
FAQs #milestoneareacom/
1. What is #milestoneareacom/?
It is a hashtag used to highlight updates, news, or conversations about the Milestone Area platform or related projects.
2. Where can I find posts using #milestoneareacom/?
Search for the hashtag on social media platforms like Twitter, Instagram, LinkedIn, and Facebook.
3. Why should I follow #milestoneareacom/?
Following the hashtag provides real-time updates, networking opportunities, and insights into related projects or events.
4. Can businesses use #milestoneareacom/?
Yes, businesses can leverage the hashtag to share news, engage with audiences, and boost online visibility.
5. Is #milestoneareacom/ trending?
Interest in the hashtag grows as more users post content, making it increasingly relevant for community engagement and updates.
TECH
twitter user demographics 2023: Age, Gender, Location & Audience Insights
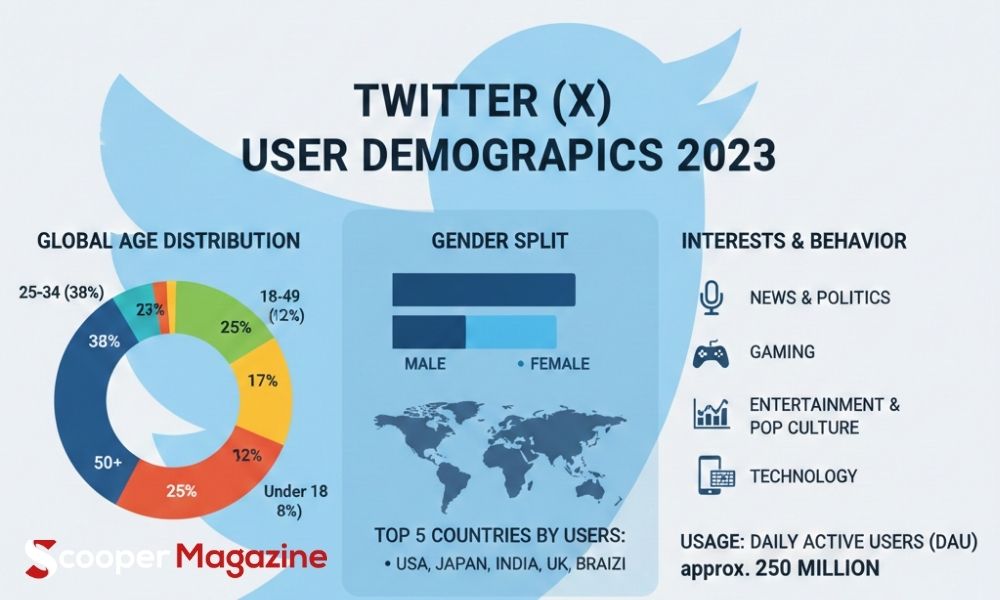
 Understanding Twitter user demographics 2023 is more important than ever for marketers, brands, advertisers, and content creators. Whether you’re launching a campaign, building a personal brand, or analyzing social media behavior, knowing who uses Twitter (now known as X) helps you create smarter, more targeted strategies.
Understanding Twitter user demographics 2023 is more important than ever for marketers, brands, advertisers, and content creators. Whether you’re launching a campaign, building a personal brand, or analyzing social media behavior, knowing who uses Twitter (now known as X) helps you create smarter, more targeted strategies.
In 2023, Twitter went through major transformations — from leadership changes to its rebrand as X. Despite these shifts, its audience remains highly influential and deeply engaged. This guide breaks down Twitter demographics 2023, including age groups, gender distribution, geographic trends, income levels, and behavioral patterns.
Overview of Twitter User Statistics 2023
Before exploring detailed segments, let’s review some important Twitter user statistics 2023:
-
Over 400 million estimated monthly active users worldwide
-
Strong user bases in the United States, Japan, India, the UK, and Brazil
-
High engagement around news, politics, sports, and tech
-
Popular among professionals, journalists, entrepreneurs, and creators
Although platforms like TikTok and Instagram dominate visual content, Twitter continues to stand out as a real-time conversation hub. Its fast-paced, discussion-focused environment keeps it relevant in today’s social media ecosystem.
Twitter Age Demographics 2023
One of the most important aspects of Twitter user demographics 2023 is age distribution. The platform tends to attract younger adults, but it also maintains engagement across multiple age brackets.
18–24 Years Old
Young adults form a strong portion of Twitter’s audience. Users in this group typically engage with:
-
Entertainment news
-
Viral trends and memes
-
Celebrity updates
-
Social activism
This demographic values fast information and cultural relevance.
25–34 Years Old
The 25–34 age group is generally the largest segment in Twitter age demographics 2023. Many professionals in this range use Twitter for:
-
Industry discussions
-
Networking
-
Tech and finance updates
-
Personal branding
This group plays a major role in shaping conversations on the platform.
35–49 Years Old
Users in this range remain active, particularly in areas such as:
-
Political discussions
-
News analysis
-
Business conversations
They often use Twitter as an information source rather than pure entertainment.
50+ Years Old
While smaller in comparison, this group uses Twitter mainly for:
-
Breaking news
-
Following public figures
-
Live event updates
Overall, the data shows that Twitter’s core strength lies within the 18–34 demographic range.
Twitter Gender Demographics 2023
Another critical element of Twitter demographics 2023 is gender distribution.
Globally, Twitter has historically had:
-
A slightly higher percentage of male users
-
A steadily growing female audience
However, engagement patterns differ by topic.
Women tend to be highly active in:
-
Lifestyle discussions
-
Entertainment
-
Social advocacy
-
Community-driven movements
Men are often more represented in:
-
Technology
-
Sports
-
Cryptocurrency
-
Political commentary
Understanding Twitter gender demographics allows brands to tailor messaging more effectively depending on their niche.
Geographic Distribution of Twitter Users
The global spread of Twitter user demographics 2023 shows strong usage across multiple regions.
United States
The U.S. remains one of Twitter’s largest and most influential markets, especially for media, politics, and trending conversations.
Japan
Japan consistently ranks as one of the most active countries on Twitter, with strong daily engagement.
India
India’s Twitter audience continues to grow, largely driven by increasing smartphone penetration and digital adoption.
United Kingdom and Brazil
Both countries show strong engagement levels and play key roles in regional conversations.
Because of its international reach, Twitter remains valuable for global campaigns and cross-border marketing strategies.
Education and Income Levels
When analyzing Twitter audience insights 2023, education and income trends stand out.
Twitter users often:
-
Have higher education levels
-
Work in professional or white-collar industries
-
Show strong interest in business and finance topics
Compared to some entertainment-heavy platforms, Twitter tends to attract users who are interested in:
-
Current events
-
Global affairs
-
Technology innovations
-
Financial markets
This makes the platform particularly attractive for B2B marketing and thought leadership campaigns.
Interests and User Behavior
One unique feature of Twitter is its real-time engagement model. Unlike platforms focused on curated visuals, Twitter thrives on conversation.
Common interest categories include:
-
News and politics
-
Sports updates
-
Technology and startups
-
Entertainment and pop culture
-
Social issues
Content spreads rapidly through reposts, replies, and trending hashtags. This fast-moving structure plays a major role in shaping Twitter user statistics 2023.
Twitter Compared to Other Platforms
To better understand Twitter demographics 2023, it helps to compare it with other major social networks.
| Platform | Dominant Age Group | Primary Use |
|---|---|---|
| 18–34 | News & discussions | |
| 18–29 | Visual storytelling | |
| TikTok | Under 30 | Short-form video |
| 25–54 | Social networking |
Twitter distinguishes itself by prioritizing conversation, opinions, and breaking updates over purely visual content.
The Rebranding to X and Its Impact
In 2023, Twitter officially rebranded to X. While this move sparked significant public attention, it did not dramatically alter core Twitter user demographics 2023.
Key observations include:
-
User interests remained consistent
-
News-based engagement continued
-
Audience structure stayed largely the same
The brand identity evolved, but user behavior patterns showed stability.
Why Twitter Demographics Matter for Businesses
Understanding Twitter demographics 2023 is crucial for businesses that want to maximize results.
Benefits include:
-
More accurate ad targeting
-
Better content tone alignment
-
Improved engagement rates
-
Strategic campaign planning
For example:
-
Tech startups may benefit from Twitter’s strong professional audience.
-
Media brands can leverage high news engagement.
-
Financial services companies can target users interested in markets and investments.
Data-driven strategies always outperform guesswork.
Emerging Trends in Twitter User Demographics 2023
Several patterns shaped the platform in 2023:
-
Increased mobile-first engagement
-
Growth in international audiences
-
Rising interest in creator monetization tools
-
Stronger emphasis on short, impactful posts
These trends reflect changing digital habits and evolving audience expectations.
Is Twitter Still Relevant in 2023?
Despite intense competition, Twitter remains one of the most influential platforms for public conversation. While growth rates may fluctuate, its impact on global discussions, media coverage, and cultural trends remains powerful.
Influence is not just about user count — it’s about conversation reach. And in that area, Twitter continues to lead.
Conclusion
The Twitter user demographics 2023 highlight a platform dominated by young adults, professionals, and news-driven audiences. With strong representation in the 18–34 age bracket and a slightly higher male user base, Twitter continues to offer unique opportunities for engagement.
For marketers, researchers, and content creators, understanding these insights can significantly improve targeting and strategy.
Even after rebranding to X, the platform remains a central space for debate, trending topics, and global interaction.
FAQs Twitter User Demographics 2023
1. What is the largest age group on Twitter in 2023?
The 25–34 age group represents the largest segment of users.
2. Is Twitter male-dominated?
Yes, Twitter generally has a slightly higher percentage of male users globally.
3. Which countries have the most Twitter users?
The United States, Japan, and India are among the top markets.
4. What are Twitter users mostly interested in?
News, politics, sports, technology, entertainment, and social issues.
5. Did the rebranding to X change user demographics?
No major demographic shifts were observed immediately after the rebrand.
TECH
ahrefs number of employees: Company Size, Growth, and Team Structure in 2025

 Ahrefs is one of the most well known SEO tools in the world. From backlink analysis to keyword research and competitor tracking, the platform has become a staple for marketers, agencies, and businesses. But beyond its powerful software, many people are curious about the company itself especially Ahrefs number of employees.
Ahrefs is one of the most well known SEO tools in the world. From backlink analysis to keyword research and competitor tracking, the platform has become a staple for marketers, agencies, and businesses. But beyond its powerful software, many people are curious about the company itself especially Ahrefs number of employees.
How big is Ahrefs? Is it a large corporation or a lean tech company? In this article, we’ll explore Ahrefs’ employee count, company structure, hiring approach, and what its team size says about its growth.
What Is the Ahrefs Number of Employees?
As of recent public estimates, Ahrefs has approximately 100 to 150 employees globally. While the company does not always publish an exact, real-time employee count, industry databases and professional platforms indicate that Ahrefs operates with a relatively lean team compared to many software companies of similar global reach.
The exact Ahrefs number of employees may fluctuate due to:
-
New hiring rounds
-
Product expansion
-
Remote team scaling
-
Department restructuring
However, it is widely known that Ahrefs runs with a compact yet highly skilled workforce.
Is Ahrefs a Large Company?
In terms of brand influence, Ahrefs feels like a massive tech company. But when looking at Ahrefs number of employees, it is considered mid-sized in the SaaS (Software as a Service) industry.
For comparison:
-
Many global SaaS companies employ 500–5,000+ people.
-
Large SEO platforms sometimes have several hundred employees.
-
Ahrefs operates with a much leaner team while competing globally.
This efficient structure is often cited as one reason for its agility and product innovation.
Where Is Ahrefs Based?
Ahrefs was founded in 2010 and is headquartered in Singapore. However, the company operates as a remote-first organization.
This means:
-
Employees work from different countries.
-
The team is distributed globally.
-
Hiring is not limited to one location.
The remote model influences the overall Ahrefs number of employees, allowing the company to recruit top talent worldwide.
Why Is the Ahrefs Team Relatively Small?
One interesting aspect of Ahrefs’ growth is that it has achieved global dominance in SEO tools without employing thousands of people.
Here’s why:
1. Product-Focused Culture
Ahrefs invests heavily in engineering and product development rather than large sales teams.
2. Minimal Venture Capital Pressure
Unlike many startups, Ahrefs has historically avoided heavy venture capital funding. This allows them to grow sustainably without aggressive expansion.
3. Strong Organic Marketing
Ahrefs generates massive traffic through its own SEO expertise, reducing the need for large marketing departments.
Because of this strategy, the Ahrefs number of employees remains modest while revenue and influence continue to grow.
Departments Within Ahrefs
Even with a lean team, Ahrefs includes multiple specialized departments:
-
Software engineers
-
Data scientists
-
Product managers
-
Customer support specialists
-
Marketing and content teams
-
Infrastructure and DevOps experts
The engineering team makes up a significant portion of the overall Ahrefs number of employees, reflecting the company’s technical foundation.
How Does Ahrefs Compare to Other SEO Companies?
To better understand Ahrefs’ scale, let’s compare:
| Company | Estimated Employees |
|---|---|
| Ahrefs | 100–150 |
| SEMrush | 1,000+ |
| Moz | 200–500 |
| SimilarWeb | 1,000+ |
While Ahrefs has fewer employees than some competitors, it competes at the same level in terms of product performance and global usage.
This highlights the efficiency behind the Ahrefs number of employees.
Revenue vs. Employee Count
Another interesting aspect is revenue per employee.
Ahrefs reportedly generates substantial annual revenue, especially considering its team size. A lean structure often leads to:
-
Higher revenue per employee
-
Lower operational overhead
-
Faster decision-making
-
Sustainable long-term growth
This makes the relatively small Ahrefs number of employees a strategic advantage rather than a limitation.
Is Ahrefs Still Hiring?
Ahrefs regularly hires for positions in:
-
Engineering
-
Data analysis
-
Customer support
As the SEO industry evolves, the Ahrefs number of employees may continue to grow gradually. However, the company appears committed to controlled expansion rather than rapid scaling.
Why People Search for Ahrefs Number of Employees
Search queries related to Ahrefs number of employees often come from:
-
Job seekers researching company size
-
Investors evaluating growth potential
-
Competitors analyzing market positioning
-
SEO professionals curious about the brand
Company size often reflects stability, culture, and long-term sustainability.
What the Employee Count Says About Company Culture
A team of around 100–150 employees suggests:
-
Close collaboration
-
Agile product development
-
Fewer management layers
-
Direct communication channels
Smaller teams often foster innovation and accountability.
The manageable Ahrefs number of employees likely contributes to the company’s strong product consistency and frequent updates.
The Future of Ahrefs Workforce
Looking ahead, the Ahrefs number of employees may increase as the company expands into:
-
AI-driven SEO tools
-
Advanced data analytics
-
Enterprise-level solutions
-
Educational platforms
However, based on its history, growth will likely remain strategic rather than aggressive.
Final Thoughts
The Ahrefs number of employees, estimated between 100 and 150, might surprise people given the platform’s global reach. Despite its relatively small workforce, Ahrefs competes with and often outperforms larger companies in the SEO space.
Its lean team structure, product-first philosophy, and remote global hiring approach have allowed it to scale efficiently while maintaining innovation.
In today’s tech landscape, bigger doesn’t always mean better — and Ahrefs proves that a focused, skilled team can build a world-class product.
FAQs Ahrefs Number of Employees
1. How many employees does Ahrefs have?
Ahrefs is estimated to have between 100 and 150 employees globally.
2. Is Ahrefs a large company?
It is considered mid-sized in the SaaS industry but highly influential in the SEO space.
3. Where is Ahrefs headquartered?
Ahrefs is headquartered in Singapore and operates as a remote-first company.
4. Why does Ahrefs have a small team?
The company focuses on product development and sustainable growth rather than aggressive scaling.
5. Is Ahrefs hiring?
Yes, Ahrefs regularly posts job openings for engineering, marketing, and support roles.
-

 CELEBRITY12 months ago
CELEBRITY12 months agoWho Is Amelia Jane Henson? Everything You Need to Know About Mia Sara and Brian Henson’s Daughter
-

 CELEBRITY1 year ago
CELEBRITY1 year agoMatt Danzeisen: The Influential Yet Low-Key Force Behind Peter Thiel’s Success
-

 CELEBRITY12 months ago
CELEBRITY12 months agoWho Is Jasmine Gong? Everything You Should Know About Brad Williams’ Wife
-

 BUSINESS11 months ago
BUSINESS11 months agoWho Is Nadia Farmiga? Everything You Need to Know About Vera Farmiga’s Sister
-

 CELEBRITY1 year ago
CELEBRITY1 year agoRachel Catudal: Everything You Need to Know About Brandon Quinn’s Wife
-

 CELEBRITY1 year ago
CELEBRITY1 year agoWho Is Gianluca Cugnetto? Everything You Need to Know About Hannah Waddingham’s Ex-Husband
-

 CELEBRITY1 year ago
CELEBRITY1 year agoWho Is Joe Alfie Winslet Mendes? Everything You Should Know About Kate Winslet’s Son
-

 CELEBRITY12 months ago
CELEBRITY12 months agoWho Is Alfred Roy Carey? Everything You Need to Know About Mariah Carey’s Father



